Towards a Cyber Defense System in Software-Defined Tactical Networks
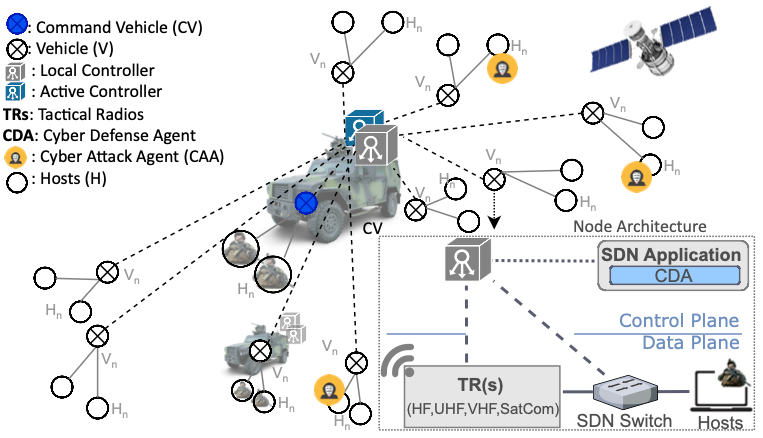
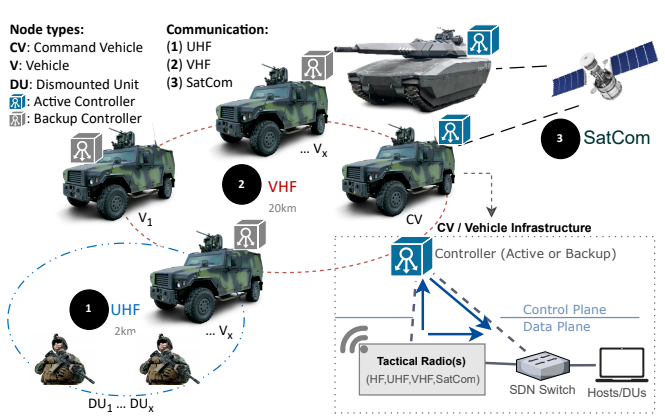
This study investigates the robustness of a Software-defined Networking (SDN) controller when confronted with a Distributed Denial-of-Service (DDOS) attack in a tactical environment. A proactive defense mechanism is introduced to detect and respond to a flooding of “packet-in” requests, triggering a response once the network features indicate an anomaly. The methodology consists of two components: the Cyber Defense Agent (CDA), consisting of monitoring, feature engineering, detection, and responses, and the Cyber Attack Agent (CAA), including the preparation, execution, and evaluation of the attack. The CDA monitors all the IP flows from the SDN controller and processes four main features such as the average number of “packet-in” requests, the response time to these requests, the entropy of IP addresses and ports for source and destination, and “packet-in” requests per switch to identify compromised switches. All the components were emulated and tested, collecting quantitative evidence to demonstrate the effectiveness of both agents.
Please cite:
@article{Kloth2024TowardsAC,
title={Towards a Cyber Defense System in Software-Defined Tactical Networks},
author={Sean Kloth and Paulo H. L. Rettore and Philipp Zi{\ss}ner and Bruno P. Santos and Peter Sevenich},
journal={2024 International Conference on Military Communication and Information Systems (ICMCIS)},
year={2024},
pages={1-8},
url={https://api.semanticscholar.org/CorpusID:270260554}
}
Sean Kloth, Paulo H. L. Rettore, Philipp Zißner, Bruno P. Santos, P. Sevenich
Founding agencies: CNPq/CAPES/FAPEMIG.
Leave a comment